So…I installed fail2ban, but…i get this:
don’t know why…?
I had something wrote up but after taking a quick look at fail2ban & thei FAQ as well as not having used it it seems to be in their FAQ about a “system time sync” issue. Hope this is of some assistance to you.
I copied this from their FAQ:
Fail2ban is running but not banning SSH bruteforce
NB:This example is based on a Debian system, but can be easily done on any distro.
The package is well installed:
*# dpkg -l |grep fail *
*ii fail2ban 0.8.1-2 bans IPs that *
cause multiple authentication
The service is running:
*# /etc/init.d/fail2ban status *
Status of authentication failure monitor: fail2ban is running
SSH jail is set up and ready:
*# sudo fail2ban-client status *
*Status *
*|- Number of jail: 1 *
`- Jail list: ssh
SSH bruteforce logs are identified by fail2ban:
# fail2ban-regex /var/log/auth.log /etc/fail2ban/filter.d/sshd.conf
…
Success, the total number of match is 30
So, check that all your logs are synchronized: all logs files (auth.log, syslog,…) must use the same time reference (if your server is not very busy, there will probably be an important difference between the output of [1]date command and the last event logged in syslog. You can force to generate a log in syslog using the logger command and check then with the output of date command)
*# date *
*Wed Nov 28 13:49:02 CET 2007 *
*# tail -2 /var/log/auth.log *
Nov 28 13:39:12 sudo: pam_unix(sudo:session): session opened for user roo
*t by (uid=0) *
Nov 28 13:39:12 sudo: pam_unix(sudo:session): session closed for user roo
t
If time reference is not the same everywhere, then fail2ban won’t ban any IP!
If you change your timezone remember to restart syslogd so fail2ban will see the correct time in the log files.
Check if backend = auto. And set backend = polling. In some cases fail2ban won’t be notified by gamin, but will chose to use it when auto is set.
Hope this will give you some idea of where to start on it.
Thank you for your research. I really appreciate it. A little over my head at the moment, but I could probably figure it out if I apply myself. However…would you take a look at this and see if you think the time is still the issue? This might be superfluous info, but I am running the latest version of Mint. I thought that if I just put a whole new distro on my machine it might solve the problem, But I haven’t been successful with that…yet. Anyway this is what I get when I execute sudo systemctl status fail2ban
OHHHH LOL!!! I figured it out! When I was watching LMS I was trying to follow along with Mr. V and fatfingered the name of my jail.local file and also created duplicate files. Got rid of those and now it works. WOOOO HOOO!!! So scary. I know just enough to be quite dangerous.
No worries @JRose!
We all learn via trial and error. By the way, don’t stick only on the video. I have attached a very explanatory PDF to that workshop. You can download it by clicking the Files on the top right of your LMS window. ![]()
And congratulations on backtracking and finding the issue!
You’re the best, Mr. V!!!
I’m always happy to help, @JRose! ![]()
I’m sorry to say I need help again, Mr. V. Installed fail2ban on a different laptop, this time running Zorin (the free version). Fail2ban won’t start, saying a log file is missing. How do I fix this?
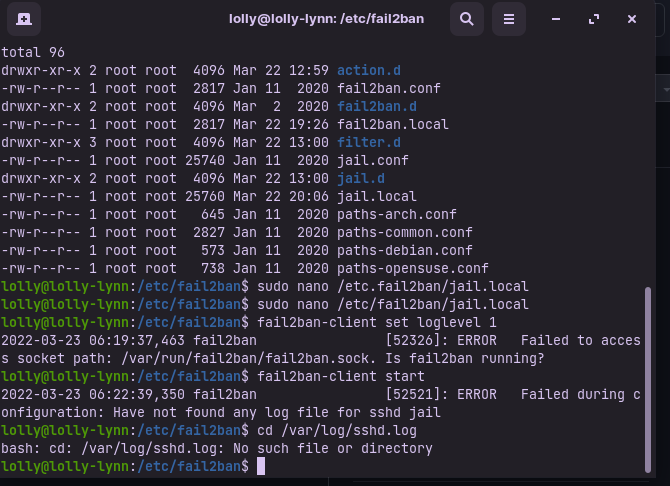
Hey @JRose!
I believe you’re receiving the first error because your service is not running. You can engage it by typing:
sudo systemctl enable --now fail2ban
Then you can normally continue with your fail2ban-client command.
Per the second issue you’re having, you’re having no SSHD logs because SSH is not installed and/or active on your system. In general, fail2ban is a useful tool for a server, where you log into via SSH and a password. This can be helpful in the following situations:
When you set up SSH keys, which we have several courses on those on the LMS, then fail2ban comes in handy for the extra security on the number 2 of the above list. Generally, having SSH keys active, assigning a different port to your SSH, and having fail2ban on a VPS will give you unparalleled security. ![]()
I hope this helps!
Thank you, Mr. V. I think it will help.